Security – Example projects
Surveillance
Infrared video is an essential security tool widely deployed for open area surveillance and intrusion detection. Resulting imagery can be processed to detect possibly suspicious persons and behaviors. 3DIR FaceMapping provides the ability to identity-tag persons who are seen under surveillance conditions, and whose images may or may not have been previously entered in any database. Operational factors such as ambient temperature and lighting, and subject parameters, such as head pose and presence of facial hair and disguises do not defeat the capability. The level of anatomical information contained in 3DIR imagery allows it to be matched against visual images in existing databases. Link analysis that combines multiple sightings of the same individual, or documents interaction with known persons, can be used to justify response actions.
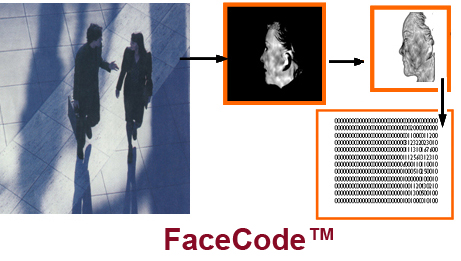
In addition to its primary advantage of producing the same excellent identification accuracy regardless of lighting conditions, ID from thermal infrared distinguishes between identical twins, and provides positive ID from profile and other views that don’t contain both eyes. Larger detector arrays now permit positive ID from substantial distance, automated pose standardization, and extraction of a FaceCode™ for each individual. That provides an ID tag for each appearance of known or unknown persons to facilitate link analysis. Pending research will evaluate the current coding method and develop the capability to aggregate code from successive image frames of a moving subject.
Shape analysis using 3D/IR imagery as a surveilled subject encounters a stimulus event (here a steep downgrade) provides additional evidence of the nature of the load carried or worn. This exercise demonstrated differences in gait, shape distortion and subject behavior when the subject was carrying what he believed to be hazardous material vs. carrying food and documents. Face and trunk areas are separately processed as shown by the highlighted rectangles.
Assessment
RedFace™ performs realtime automated detection of attitude akin to FACS (facial action code system) which requires extensive training. Paul Ekman systematized a method for detecting a person’s true feelings about conditions or events. His exhaustive study of facial muscles linked very small, very fast changes in facial expression to specific attitudes. He developed a course of training for persons seeking to develop a capability to “read faces” using his Facial Action Coding System (FACS), which he claims is universal to all cultures. Although the technique is widely known, becoming skilled requires lengthily practice plus an innate ability to see subtle changes. Few people have become accomplished at the system, and no automated version has been developed for processing of visible light video. The except shown from the FACS Manual illustrates one of the microexpressions to be detected. Considering that this facial appearance may persist for a small fraction of a second only, it is remarkable that some people have developed expertise.
RedFace analyzes frame-to-frame microthermal changes across the facial area. Key to being able to automatically detect microexpressions is the ability to automatically register successive frames precisely using FaceMaps. Muscle tension which produces the facial actions of Ekman generates minute amounts of heat which is detected by a sufficiently sensitive IR camera. Conducting controlled experiments is difficult to elicit true spontaneous microexpression reactions. Imaging players using both IR and VL high-speed cameras during a high stakes poker game could provide a good test of the method. If successful, it could provide a training method for professional players.
Counterfeit Detection
Counterfeit electronic devices are a significant hazard in medical products as well as in defense equipment. Thermal IR imaging with FlashCorrelation® optical processing offers product authentication and counterfeit detection with certain advantages to that provided by DNA marking. Processing utilizes thermal 3DIR images to analyze: toolmark characteristics, applied and hidden marks, intrinsic features, embedded elements, materials composition, comparison to known authentic items allowing for manufacturing tolerances and wear.
Semiconductor manufacturing companies spend billions of dollars per year to design and manufacture products to the highest quality and reliability levels. Wafer fabrication laboratories are some of the most expensive facilities in the world, meaning semiconductor and integrated component manufacturers must invest billions to develop and maintain quality control of their products. Other companies can produce cheap counterfeit versions of the products, generate large profits quickly, and face little risk that management will be prosecuted. In addition to the profit motive, counterfeiters who produce inferior products may be motivated to financially damage the original manufacturers, cause human injuries, or destroy infrastructure.
A single faulty counterfeit component may cause failure of aviation, medical, military, energy, communications or transportation systems. The Semiconductor Industry Association estimates that counterfeits cost U.S semiconductor companies more than $8 billion annually in lost revenue, and results in the loss of 11,000 American jobs. The cost of equipment failures, corporate liabilities, and reputation damage from failure to remove counterfeits from the manufacturing process stream can be significantly greater than the cost of implementing effective authentication procedures at each step in the procurement through manufacturing process.
The Defense Department has supported use of DNA-marking to securely encode identifying information on the surface of items for future authentication of components and integrated assemblies. This requires development of unique DNA taggants for each manufacturer or product. Then determining where and how the taggants will be applied. Security of the process depends on it being difficult or impossible to reproduce the DNA and on procedures to secure the DNA material against its being used on counterfeit items. The logistical complexity of using DNA-marking, its restricted availability and its high cost has spurred resistance from semiconductor manufacturers and interest in development of other authentication techniques.
IRID’s authentication method uses 3DIR imaging, with spectral filters, to read surface area codes created by toolmarks with or without overlaid patterns. Multiple pattern layers can be added to update the information, while allowing every prior layer to be read in parallel. As an example, for electronic components and assemblies, surface area codes can embed unique item identification, part number, batch number and date of manufacture. Layers can be added to indicate when tests are completed or further processing performed. Overprinted layers need not be precisely aligned. Read-out does not require controlled angle and distance parameters. The composite multi-layered coded area can withstand obliteration of more than 60% and still be correctly read in full.
Readout utilizes FlashCorrelation® (FC) which is a highly efficient patented technique for identifying complex 2D and 3D images, including toolmarks with overlaid patterns. It creates authenticating 3D patterns on demand, of any size and shape including curved surfaces. Its security does not depend on controlling pre-manufactured labels and tapes which can be counterfeited, and will be if the potential value of doing that is sufficiently high. The IRID technique has been used to produce and read multi-layered embedded and applied authentication labels, offering more security and durability than current marking technologies including tamper evident security seals and security tape, holographic foil security labels, and color-changing films.
Commercial security seals and tape
3-layer IRID Security Label